Setting up the hidden service
You can update your choices at any time in your settings. A first wave of liberalization took place in South America, after Chile liberalized its energy market in 1980. No response to a support ticket. He has been using computers for 20 years tinkering with everything from the UI to the Windows registry to device firmware. Passports or drivers’ licenses – and filter or sort by the item’s price. Those on RaidForums traded in personal data records of U. You can also test if you are able to access other onion services by connecting to DuckDuckGo’s Onion Service. The website has now been seized by court order. Otherwise, someone may be ableto correlate your hidden service with the public one. J CODE entities, including the FBI, U. Our current Round It Up partner is The Giving Tree. From white house i was able to get vendor bond waived on almost every other market place’. Paul Ducklin is a passionate security proselytiser. The concept of account abstraction dates back to at least 2016 and refers to the idea of treating both externally owned accounts like wallets and smart contract accounts similarly, thereby simplifying the user experience. Postal Inspection Service, and HSI investigated the case. Torch is the oldest and largest. 07 and BTC market dominance is 49.
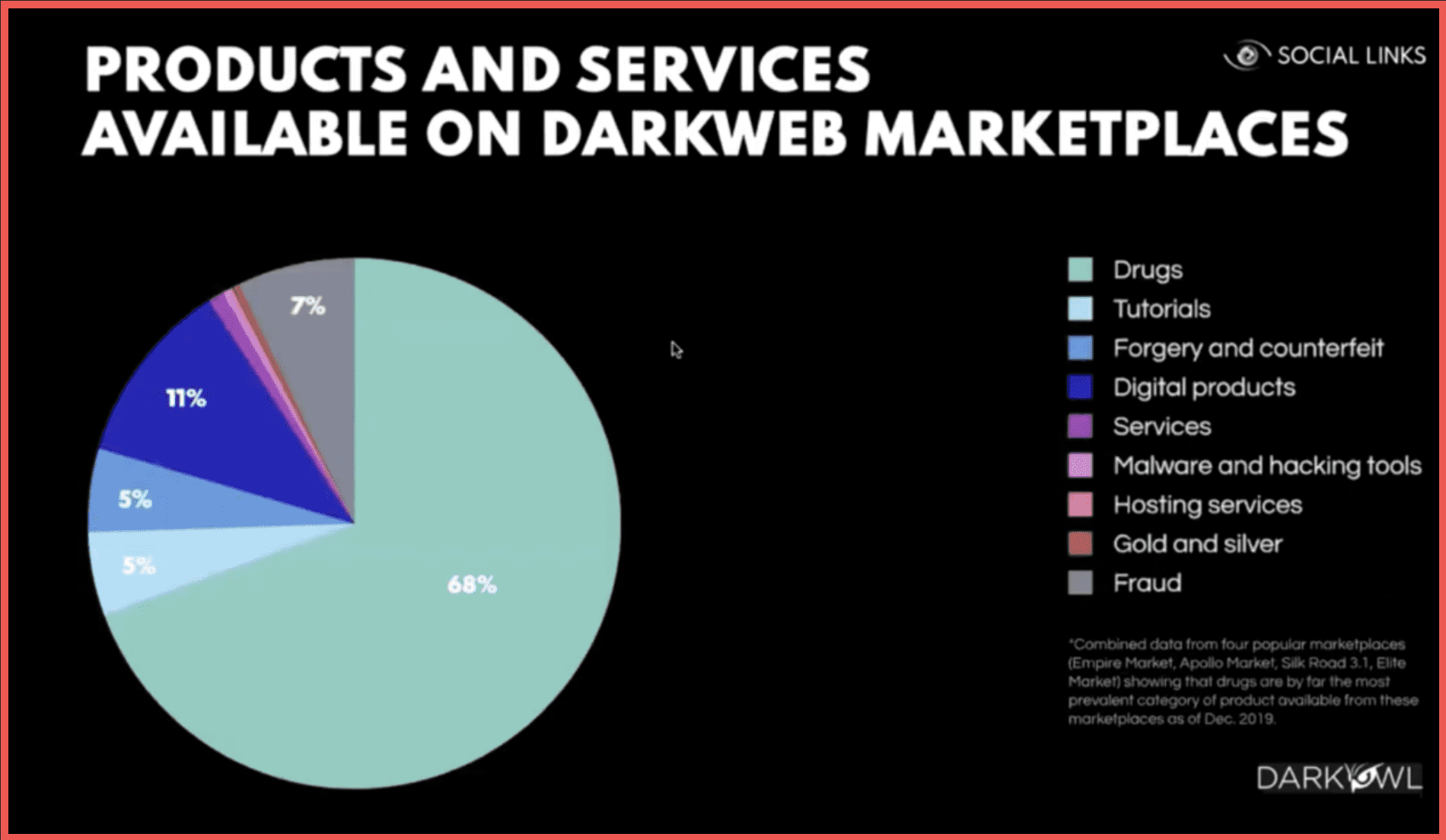
Genesis Market sold to anonymous buyer despite FBI disruption
Shopping online with Monero is like being a secret agent on a mission to buy awesome stuff. Ulbricht is alleged to have agreed to pay $80,000 to the undercover agent for the murder of the employee. As a result, the forum is still active, but its future may seem uncertain. Forum moderator if no login was made on that server within X amount of days. Tails is designed for end users who need anonymity Nemesis marketplace and a way to boot a system without leaving a forensic evidence trail. Infrastructure like that is both dangerous and illegal to access. Flare continously scans the internet for exposed enterprise assets and prioritizes alerts so you can take action in real time. The joint project PANDA on which this publication is based was funded by the Federal Ministry of Education and Research under the funding codes 13N14355 and 13N14356. The report shows that the percentage of a region’s share of drug focused vendor activity matches very closely with what is known about the global drug trade. Customs and Border Protection CBP; the DEA’s Baltimore District Office; USPIS Washington Division; the U. The interfaces often resemble conventional online marketplaces, but the products and services offered are far from ordinary. As the ecosystem evolves and Ethereum continues to upgrade, Layer 2 solutions are anticipated to attract significant capital and user activity, possibly triggering a new bull run in the Layer 2 space as they offer more scalable and efficient blockchain solutions. Since it was first launched in 2014, ProtonMail has risen to be one of the most recommended and trusted private email providers it also has a high quality VPN but that’s a topic for another post. Therefore, the service randomly picks some relays, builds circuits to them, and asks them to act as introduction points by telling them its public key. Cybereason is celebrating International Women’s Day and Women’s History Month through education, activities and events, and we invite all Defenders to join us as we work together to BreaktheBias. We could see a new DWM called Kraken Market, which several DWMs will prepare as the real successor of Hydra in the next year.

Not perfectly private
Russian Market is a hacker focused website with high volumes of stolen information available. Forum should be target number 1 to intercept. And get a VPN to protect your privacy wherever you browse online. 2007; Bakke and Whited, 2010; Edmans et al. Add the following lines in the editor window. Police announced in March an eight month investigation resulted in the closure of the Dream Market, which specialized in the sale of narcotics and stolen data. They also hide their location, ownership, and other identifiers. NFT sales will fund the restoration of physical monuments in Ukraine. Showed the number of authentic onion addresses and the number of phishing addresses using two darknet marketplaces and three bitcoin mixer sites as examples. Suggested Citation:Suggested Citation. Most of all services, that a crawler cannot reach belong to botnet command and control addresses.
SPECTRUM AV INDIA
ASAP Market represents new era, next generation marketplace. To understand what DNMs are and how they operate, it’s important to first clarify that there are actually three different layers of the Internet. Importantly, the monthly brokerage trading data we compile are published by TSX and thus our analysis neither suffers from the difficulty of accessing proprietary trading records nor from the econometric challenges in estimating alternative proxies. DOI: ARES 2022: The 17th International Conference on Availability, Reliability and Security, Vienna, Austria, August 2022. And now after googling the names Faire and seeing all this information about what they are and how they contact other companies customers via email never mentioning of course who or how they got your email in the first place. Everything I ordered was delivered in short time. Either by using a web crawler or by using the DHT approach. The darknet market landscape is constantly evolving, driven by technological advancements, law enforcement pressure, and the ever changing demands of users. Dave W verified owner – 14/11/2022. » Prior to the takedown, AlphaBay hosted 40,000 vendors selling 250,000 illegal products to 200,000 registered users. Which parts of cybercrime value chains are successfully commoditized, and which are not. As prosecutors stated following the recent DarkMarket takedown: « Investigators expect to use the data saved to launch new probes against the moderators, sellers and buyers of the marketplace. Therefore once a single hidden service has hit the limit of vertical scaling getting faster CPUs there is not the option of horizontal scaling adding more CPUs and more computers. The Tor Anonymity System’s key functionality `Hidden Services’ allows users to set up anonymous information services like websites that can only be accessed through the Tor network and therefore are protected against identification of the host that runs the services. Guide how to access Nemesis market. We just sent you a confirmation email.
![]()
Digital Edition
It also means it’s hard to locate and shut down servers that fall foul of the law. The authors are responsible for the content of this publication. Its name is derived from SIGINT « Signals Intelligence », which refers to intelligence gathering by intercepting signals. Hydra vendors offered a variety of illicit drugs for sale, including cocaine, methamphetamine, LSD, heroin and other opioids. While classified government data and sensitive health records sit in the deep web, many of the sites we use everyday are also part of the deep web, such as our email accounts and personal banking portals. The way in which a sample is compiled is crucial to the research, as it serves as the basis for any subsequent analysis. Over four weeks, I invited both artisans and buyers who had experience with Faire to take part in a survey to collect feedback from this community and measure the results makers see on the platform. CoinDesk operates as an independent subsidiary, and an editorial committee, chaired by a former editor in chief of The Wall Street Journal, is being formed to support journalistic integrity. Was told to mark it as received and then tell them what was missing. A significant trend in the global Dark Web Intelligence market business involves introducing product categories encompassing different types TorThe Onion Router, I2PInvisible Internet Project and applications BFSI, Education, Energy, Government, Healthcare, Transportation, Manufacturing, Others to meet the demands of the swiftly expanding sector. Treasurers and CFOs are worried about how their FX tech will cope with a potential increase in hedging activity. Indeed, we show that we can correctly determine which of the 50 monitored pages the client is visiting with 88% true positive rate and false positive rate as low as 2. The anonymity of the dark web is also a big benefit for whistleblowers submitting sensitive information to news outlets. Citizens organizing protests during Arab Spring, the darknet is also a convenient place for illegal content such as DNMs, Child Sexual Abuse Material « CSAM », hacking forums, fraud forums, and money laundering forums. Cd /var/lib/tor/hideme/. The Justice Department announced today the seizure of Hydra Market Hydra, the world’s largest and longest running darknet market. Table 3 shows all marketplaces and the number of found onion addresses through which these marketplaces can be reached. On a recent visit to Dread, we discovered that the ViceCity dark web market was in the middle of an exit scam. We will continue to investigate, expose, and take action against criminal networks no matter where they operate. Endogenous Matching and the Empirical Determinants of Contract Form. It may look like a conspiracy theory, but since September 2019 many TOR users have limited their trust in the D. The market now has an established reputation among cybercriminals, which means that any stolen credentials for sale on there are likely to provide valid access to systems, services, or apps. Upon starting Tor for the first time with our new configuration, an. However, in July 2017, AlphaBay suddenly went offline. Once those three Tor circuits are in place, the hidden server can publish the data necessary to connect: the introduction points and the identifying data required to cryptographically assure that communications directed to that hidden service arrive there. From this perspective, vendors may be attracted to marketplaces from which they can also source their products more efficiently.

How To: Write an XSS Cookie Stealer in JavaScript to Steal Passwords
The platform offers a seamless and secure browsing and shopping experience, protected by robust security measures. Alphabay Market was originally operating from 2014 to 2017 with alpha02 and DeSnake as admins and was the biggest darknet market in history. Have a question about Government Services. A percentage indicates the actual size of the Tor darknet estimated by the authors compared to the total number of existing onion addresses. Let’s also embrace Tor. 2014, and reputation takes on a higher market value after a disruption Duxbury and Haynie 2020. Through their platform, users can see how the web will change in the coming years. Meanwhile, some see bitcoin as a sort of « safe haven » asset to pour money into in times of geopolitical strife. Before making a purchase, make sure you research the seller and the product. While not the biggest dark web marketplace for hackers, it’s still not a bad idea to monitor this site due to its continued growth. If you want to access regular HTTPS websites on the surface web via the Tor network for added privacy and anonymity, DuckDuckGo is what you need. Thus, for both nodal covariates described—number of vendors and price change—we examine the impact of the nodal attribute on out degree the likelihood a market will send high out flows of vendors to other markets, and in degree the likelihood a market will receive high in flows of vendors from other markets, allowing us to disentangle vendor decisions to leave old markets, from vendor decisions to join new ones.
Get papers listed
As such, they are normally under intense scrutiny from law enforcement and security professionals alike. The most noticable change is the increase in address length, however Onion v3 uses better cryptography, ECC eliptic curve cryptography rather than RSA, and has an improved hidden service directory protocol. 449 and the clustering coefficient to 0. Crypto is not insured by the Federal Deposit Insurance Corporation or the Securities Investor Protection Corporation. I think this one has a future. « Other solutions would present us with thousands of potential leaks which were impossible to work with for our small team, Flare was the only one that could successfully filter and prioritize data leaks with their 5 point scoring system. Postal Inspection Service is dedicated to protecting the United States mail from being used to transport illegal drugs and illicit goods available on the darknet, » said Chief Postal Inspector Gary R. If nothing happens, download GitHub Desktop and try again. B: The deep web consists of sites that require a login to access email accounts, banking portals, subscription services. Learn more in our Cookie Policy. Before you learn about safeguards against the crypto Bull Run coming in 2024 or 2025, it is important to familiarize yourself with its definition. Please update to get the most out of Flickr. Pretty Good Privacy PGP is a popular program used to encrypt and decrypt email over the Internet, as well as to authenticate messages with digital signatures and encrypted stored files. 2019, and more recent applications on where offenders move to Hatten and Piza 2021. How to get access Nemesis marketplace with Tor browser onion link. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. New hidden wiki updated for 2024. A while back I made another blog post on PGP keys which helps explain what PGP is and how it works. Anonymous Trading Customers and Sellers. Many crime groups use the dark web to access and share certain types of content, making it a risky place to be. In October, CrowdStrike announced Falcon X Recon, a new module in its threat intelligence offering that provides « situational awareness » by going « beyond the dark web to include forums with restricted access on the deep web, breach data, source code repositories, paste sites, mobile greyware stores, unsecured cloud storage, public social media posts and messaging apps, » according to its press release announcement. Popular NFT launch on Ethereum loses $34 million in faulty smart contract. Standard Chartered Bank’s bitcoin prediction, as reported in CoinDesk, is that the cryptocurrency will reach USD 100,000 by the end of 2024. Every search result shows you a brief product description, high resolution image, the purchasing options all quantities and prices in a single listing unlike many markets which have duplicates everywhere and information about the vendor such as their rating, sales and shipping from location. Deep web sites have to be hosted somewhere, and Impreza Hosting is one of the most secure and anonymous dark web hosting services. When examining onion services in terms of content, it is crucial to check the exclusion criteria of the analysis. If you wanna lose your money, give it to Nemesis.
Report sent
For more information, please see our Cookie Notice and our Privacy Policy. Hacking vendors commonly offered to illegally access online accounts of the buyer’s choosing. Though the drug transactions were limited to Russia and its geographic neighbors, the cyber and money laundering tools were available to anyone in the world willing to pay. Consult an attorney or tax professional regarding your specific situation. Which parts of cybercrime value chains are successfully commoditized, and which are not. Check out the updated agenda at: nsBElena Rey Anna Neistat Stephen Palley Yoav Navon Thomas Goodhead James Collins Q. I think this one has a future. A host is basically a website’s house, or where it lives and takes up space. These illegal shopping platforms, which gained popularity in the dark web in 2011 with Silkroad, which we call the first modern DWM, have increased their activity until today. In addition, Ahmia and Haystack make every effort to filter out and blacklist sites known to contain harmful, abusive, or illegal content. There’s a lot happening in the world. By clicking Agree and Join, you agree to the LinkedIn User Agreement, Privacy Policy, and Cookie Policy. Our Team of experts is available around the clock and ready to asist. Fucking bottom feeder. Cybercriminals have started actively using Tor to host malicious infrastructure. BTC deposit never arrived. This article takes you through the top five dark web marketplaces currently worth keeping track of for potential threats in 2023. 7 billion – belonging to their customers. Poisson exponential random graph models predicting vendor flows between digital marketplaces. Assistance was also provided by the Justice Department’s National Cryptocurrency Enforcement Team. The post Top 5 Dark Web Marketplaces appeared first on Flare Cyber Threat Intel Digital Risk Protection. An additional 10 feet is an additional $100. Facebook provides an Onion Site for this very reason. Threat Command can help identify threat actors and their intentions with broad coverage of dark web sources. Mushrooms have been my goto meat replacement. Avast SecureLine VPN encrypts all of your internet traffic to block hackers and keeps snoops out. If you are a registered author of this item, you may also want to check the « citations » tab in your RePEc Author Service profile, as there may be some citations waiting for confirmation. Onion » top level domain instead of « .
Reports
Here you’ll find all collections you’ve created before. You will be alerted when a vendor accepts and ships an order. It features a unique site design unlike any other market yet is still intuitive and easy to use. I had an old two piece, traditional, clamp but found it annoying to fiddle around with it to get it in the right position and not hitting the Mover. Rely on our team of analysts to monitor your adversaries and engage with threat actors. The DEA’s Miami Field Division, FBI, IRS CI, U. Despite the optimistic outlook, the crypto market will likely face challenges. This trojan horse enables an outsider to then control, alter, or view traffic flows between the app or website and a victim’s mobile device. You provide your tent, tables and chairs. If you don’t have a FX Markets account, please register for a trial. On the one hand, our market knowledge and desirable standard products. Even Stealer as a service SaaS, one of the most recent cyber attack vectors, has taken its place in black markets. The operator of the website was also arrested on federal criminal charges. Our Team of experts is available around the clock and ready to asist. OnionLand is also the name of a prominent site that acts as a major search repository for finding items on the dark web. For the BITW Fund, which has Shares available for trading on the OTCQX Best Market, there can be no assurance that the value of the Shares, if traded on this secondary market, will reflect the value of the BITW Fund’s net assets. This study examines darknet markets through the lens of a business theory on knowledge management. Onion is one of the essential ingredients of daily life in Bangladesh. Now you’d want to change torrc. Delft University of Technology. Innocenti: The challenges that we face are, even when these pills are created and shipped around the country, well, now those pills are being resold in some instances to people in high school, people at universities. Nemesis Market, a clandestine network market, is meticulously orchestrated around the vendor community duality, assimilating characteristic fragments from its predecessors into a distinctive amalgamation of a marketplace and discussion board. All you have to do is click the 5 squares which don’t match the rest of the image. Metrics record slightly more than 60,000 unique. Without diving into all of those steps, I do want to list a few general purposeguidelines here. Progress can be monitored on a dedicated website on the Tor network created by the Dutch National Police politiepcvh42eav. This output contributes to the following UN Sustainable Development Goals SDGs. I received 91 responses: 83% of those were from artisans, 9% were from retailers, and 8% of respondents both bought and sold on Faire.
So when do we all start accepting that high inflation isn’t a thing any more?
« Working closely with domestic and international law enforcement, the FBI and our partners have taken action to disrupt several websites dedicated to the buying and selling of illegal drugs and other unlawful goods, » said FBI Executive Assistant Director Anderson. It’s crucial to keep in mind, though, that many of the acts performed on these platforms are illegal and unethical. HTTPS requires you to get a valid certificate forf27sojd8aymqqtwa. 5% of all hacked account listings, followed the top line trends more closely. This is the ToRat server, a part of the ToRat Project. The criminal group behind the cyber fraud platform Genesis Market claimed on Thursday that it had been sold to an unidentified buyer a few months after U. This approach theoretically reduces the likelihood of scamming and law enforcement operations. The stolen data supply chain begins with producers – hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information and Social Security numbers. Inaugurated in Lisbon in 1995, it is one of the EU’s decentralised agencies.

 Tableau Khawatir Hamasat
Tableau Khawatir Hamasat  Tableau Decoratif Khawatir
Tableau Decoratif Khawatir  Tableau Decoratif corklid
Tableau Decoratif corklid  Tableau Decoratif RAID
Tableau Decoratif RAID  Tableau Décoratif Khayal
Tableau Décoratif Khayal